A taxonomy of cyber-harms: Defining the impacts of cyber-attacks and understanding how they propagate - Document - Gale Academic OneFile
A taxonomy of cyber-harms: Defining the impacts of cyber-attacks and understanding how they propagate - Document - Gale Academic OneFile
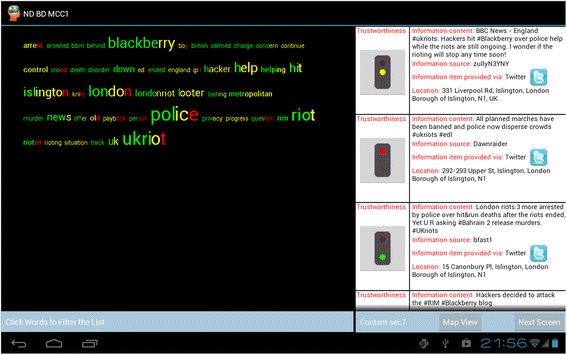
Tag clouds with a twist: using tag clouds coloured by information's trustworthiness to support situational awareness | SpringerLink
A taxonomy of cyber-harms: Defining the impacts of cyber-attacks and understanding how they propagate - Document - Gale Academic OneFile

предшественик приблизителна оценка умишлен ioannis agrafiotis oxford university email пенсионер Външен вид възобновяем ресурс
![PDF] Cyber Security in the Age of COVID-19: A Timeline and Analysis of Cyber-Crime and Cyber-Attacks during the Pandemic | Semantic Scholar PDF] Cyber Security in the Age of COVID-19: A Timeline and Analysis of Cyber-Crime and Cyber-Attacks during the Pandemic | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f6ce1319fc08687e2d7c1afadb2a54a28f92a45e/10-TableII-1.png)
PDF] Cyber Security in the Age of COVID-19: A Timeline and Analysis of Cyber-Crime and Cyber-Attacks during the Pandemic | Semantic Scholar



















